Knowledge Base

Introduction
This knowledge base will help you adapt the policies, procedures, and resources provided by Frontline Policies. It is vital that your organisation does this to reflect its specific profile, ways of working, and location. This process should involve a wide range of co-workers and other stakeholders in your organisation.
We have de-mystified the language and methodology of security risk management throughout Frontline Policies. Nonetheless, some elements of the security framework can be complex and need to be carefully thought through. If you need help, please request support from Open Briefing.
This project was made possible thanks to the support of the National Endowment for Democracy and Oak Foundation.
Structure
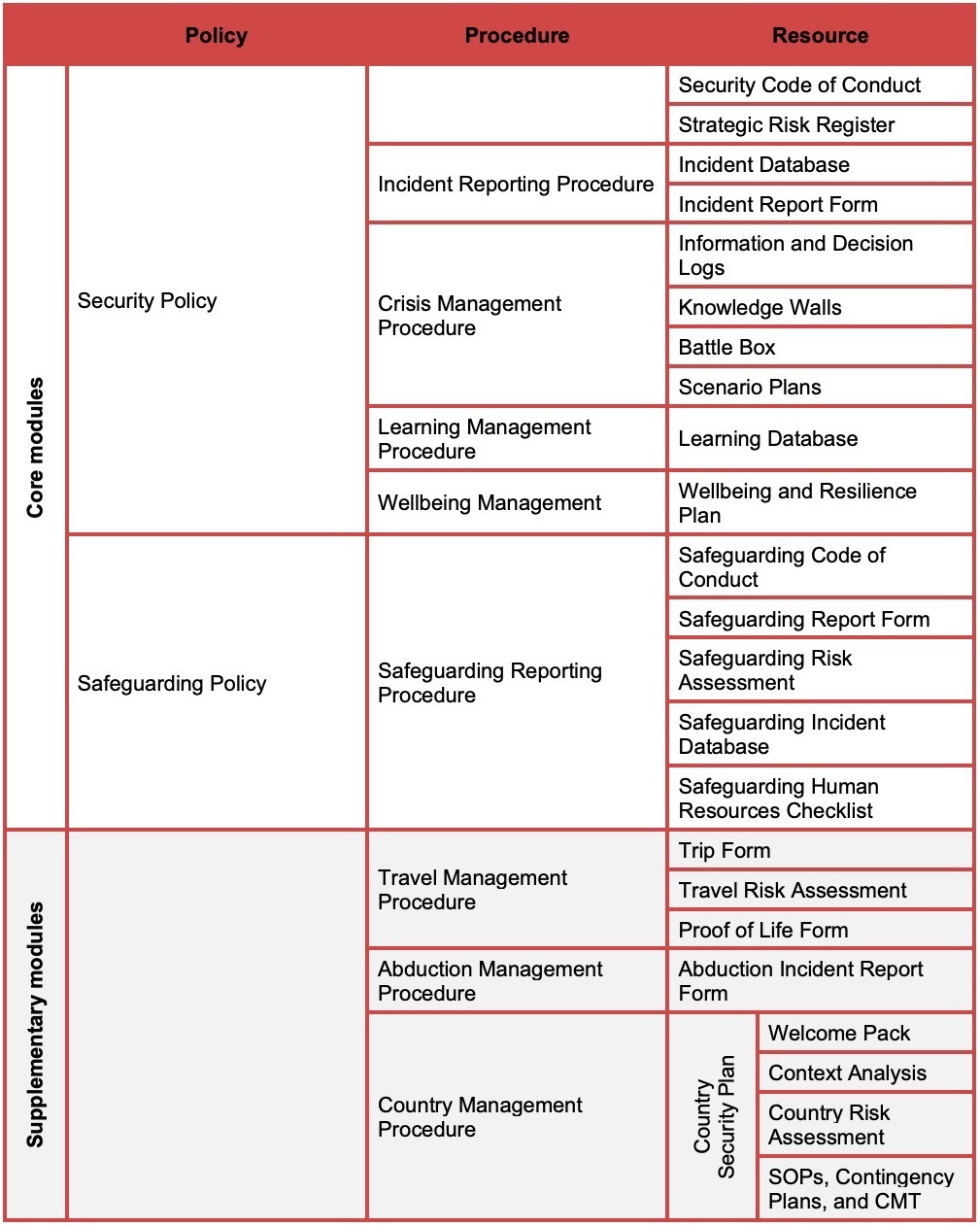
The security risk management frameworks built by Frontline Policies consist of policies, procedures, and resources. These three types of documents differ in important ways:
Policies identify the legal and moral responsibilities and commitments that organisations have and the ways that we will manage them in a systematic way.
Procedures detail how we will achieve the commitments made in the policy.
Resources are the forms and other tools that we use to implement the procedures.
Your framework will consist of seven Core Modules made up of two policies and five procedures plus a number of resources. You may also have up to three Supplementary Modules depending on the answers that you provided in Frontline Policies.
Unless stated otherwise in this guidance, you should amend each section of the framework to better fit your organisation's profile, ways of working, and location.
In order to continue to meet best practice and reflect any changes in applicable law, you should also review each procedure at least once every two years.
Approach
Decisions about security risk management are made by and affect people. Two categories of people are integral to the approach taken in Frontline Policies:
‘A Senior Person’. It is important that decisions with respect to security risks are taken by a suitable people in your organisation. Throughout the policies, procedures, and resources, many decisions are allocated to a ‘Senior Person’. When adapting the documents, we recommend that you replace this text with the title of an appropriate role within your organisation, such as the executive director or other senior manager.
‘Those who work on our behalf’. While there may be specific things that your organisation needs to do to meet its legal duty of care obligations for employees, it may be less clear for consultants, volunteers and others who you work with. There may be donor requirements or contractual obligations, but it is largely your organisation’s moral choice regarding what you want to provide for non-employees. Therefore, you may choose that some policies, procedures, or resources only apply to employees (e.g. learning management procedure), while others may apply to employees, contractors, consultants, volunteers, suppliers, and any others who work on your organisation’s behalf (e.g. Safeguarding Policy).
Security Policy
Purpose: In the Security Policy, your organisation accepts its duty of care obligations; identifies its risk appetite, strategies, and principles; details its risk management responsibilities, duty bearer commitments, and crisis management commitments; and sets out its risk management methodology.
Our duty of care
This section is an important accountability statement. It states that your organisation has a duty of care (legal, moral or contractual) and recognises this as an obligation. It also states that your organisation seeks to reduce risk and effectively respond to incidents.
Non-compliance
This section states that any failure to follow the Security Policy and the other elements of the security framework will be considered a disciplinary matter, which may result in disciplinary action up to and including termination of contract. This is included to allow your organisation to act when those who work on your behalf refuse to follow your organisation’s security risk management procedures and all other forms of encouragement and training have failed.
Risk appetite
This is a critical section of the Security Policy. Your organisation’s risk appetite needs to be confirmed and communicated so that your organisation can achieve the following:
Meet best practice (and in some cases legal requirements)
Provide clear parameters for your co-workers
Systematically assess and manage risk
Protect the organisation
Your organisation’s risk appetite must be as follows:
Measurable. This is achieved through risk registers and risk assessments.
Related to capacity. The higher your risk appetite, the higher must be your capacity to manage and respond to risks.
Integrated with control mechanisms. This is achieved through the strategies and mitigations applied in your risk registers and risk assessments.
Reviewed. An organisation’s risk appetite will fluctuate over time for many internal and external reasons.
To help you structure your risk appetite statement, it has been broken down into the three sections described below:
Risk appetite statement. This section identifies why your organisation and co-workers are exposed to risk and indicates your primary risk management approach (you can choose to avoid, manage, transfer, or accept risk). It further states that your organisation uses a systematic risk management methodology and indicates the level of risk above which you are not willing to go (you can choose VERY LOW, LOW, MEDIUM, HIGH, or VERY HIGH).
Operating above our risk appetite. This section describes how your organisation approaches ‘criticality’. This sets out that your organisation may, on occasion and for good reason, accept risks higher than those stated above. If it is possible that your organisation will do this, then you need to detail the factors that will be considered and whose approval will be required for the final decision.
Achieving our risk appetite. This section states that your organisation uses measurable indicators (present in your risk assessments and risk registers), allocates security and risk management strategies, and ensures that risk decisions are taken at the appropriate levels of management. All of this is detailed to evidence a systematic approach.
If you indicated that you either operate in or travel to hostile environments, your policy will also include a ‘Risk Ratings’ and ‘Minimum Standards’ section, which relate to your Travel Management Procedure and/or Country Management Procedure.
Principles
Your organisation should approach the management of security risks with a set of principles. You may wish to develop your own principles and/or remove some of the suggested ones; however, we would strongly advise against removing ‘Primacy of Life’ and ‘Freely Decline’ as these specifically relate to common legal requirements.
Strategies
Different organisations will need to adopt different security risk management strategies to ensure risk reduction in appropriate ways. Organisations may also prefer to adopt a ‘hard’ or ‘soft’ approach to managing security risks. Commonly, in rights-based or humanitarian organisations, softer strategies like low profile and network leverage are preferred over harder strategies like armed deterrence or close protection.
In this table, you can remove or add to the example strategies provided. We strongly advise that you indicate a most preferred and least preferred strategy. Some organisations may wish to add a specific sentence to indicate that the use of weapons – armed deterrence – is not allowed (unless under specific circumstances, if agreed, when they must be approved by a Senior Person).
Responsibilities
This section details who is responsible for which security risk management tasks. These responsibilities have been split as follows:
Risk owners. Those accountable and responsible for the risk in your organisation.
Risk managers. Those who operationally manage the risk in your organisation.
Risk exposed. All those who work on your behalf.
Please review and add or delete the responsibilities for the risk owners, managers, and exposed so that they are appropriate to your organisation. For the risk owners and risk managers, please indicate the role of the person responsible, e.g. executive director.
Duty of care commitments
This section details what commitments you make to each ‘duty bearer’ in your organisation. A duty bearer is a category of people for whom you have a duty of care; examples might include employees, consultants, volunteers, and suppliers. You may want to use different, more specific categories, such as international employees, national employees, long-term contractors, short-term consultants, volunteers, consortium partners, implementing partners, and suppliers.
To complete this section, do the following:
Decide who your duty bearers are and enter them into the columns in the top right.
Review the commitments under each section (security governance, travel and crisis management, partners, and donors), amending commitments to fit your organisation, work, and location.
Adjust the checkmarks to ensure that each duty bearer has been assigned the correct commitments.
Increased exposure
An individual’s exposure to risk depends on the interaction between multiple factors, such as follows:
Individual (e.g. ethnicity, gender, sexual identity)
Organisational (e.g. seniority of role, activities of your organisation)
Operational (e.g. role purpose, access to sensitive information)
Contextual (e.g. social attitudes to your cause or organisation)
Some individuals who work on your behalf will have increased exposure (vulnerability) to risk as a result of one or more of these factors. As such, it is not enough to apply a ‘one-size-fits-all’ approach to security risk management. In your risk assessments and security risk management practices, your organisation needs to identify the above-mentioned factors and implement mitigations to reduce the risk for all people who work on your behalf but particularly those who have increased exposure to risk. Please amend the table to further tailor your Security Policy.
Crisis management
This section details (depending on your answers) your organisation’s policy approach to domestic relocation and international evacuation for security and medical reasons. Please review this section and amend as appropriate.
Annex 1 – Risk management methodology
This annex to the Security Policy details your risk management methodology in four phases:
Phase 1 – Context
Phase 2 – Assess
Phase 3 – Control
Phase 4 – Monitor
You may wish to adapt this section to make it more relevant to your organisation, work, and location; however, any updates will also need to be reflected in other documents in the framework (e.g. Strategic Risk Register and risk assessments).
Security Code of Conduct
Purpose: The Security Code of Conduct codifies the security-related behaviours that those working on your behalf must understand and follow.
It is split into two sections:
Background. Why the Security Code of Conduct is important and the consequences of not following it.
Agreement. What those who work on your behalf agree to by signing the document.
Please work through the agreement section and amend as appropriate. Once you have a final version in place, it should be signed by all those who work on your behalf and integrated into recruitment and contracting processes.
Strategic Risk Register
Purpose: Strategic risks are those that are likely to affect your entire organisation rather than an individual staff member. This might include reputational damage, legal action, major fraud, and so on. The Strategic Risk Register is used to record these threats, your assessment of the risk that they pose, and the mitigations in place to reduce the risk. As the Risk Register is for risks at a strategic level, it should be completed by the Senior Person or Senior Management Team and reviewed regularly (ideally quarterly).
To complete the Strategic Risk Register, follow these steps:
List the threats that could harm your organisation and describe why your organisation is vulnerable (exposed) to each threat.
Look at the Scoring Definitions tab to decide likelihood and impact scores (without implementing any mitigations) and enter either 1 (VERY LOW), 2 (LOW), 3 (MEDIUM), 4 (HIGH) or 5 (VERY HIGH) for each using the dropdown.
Identify measures already in place to reduce the likelihood and impact of your organisation being harmed. Focus on reducing your organisation’s vulnerabilities (exposure).
Look at the Scoring Definitions tab to decide the likelihood and impact scores (after implementing the mitigations) and enter either 1 (VERY LOW), 2 (LOW), 3 (MEDIUM), 4 (HIGH) or 5 (VERY HIGH) for each using the dropdown.
Identify if the risk is a ‘standing’ risk (e.g. safety and security) or a ‘temporary’ risk (e.g. a court case) using the dropdown.
Identify the risk management strategy your organisation will adopt (accept, avoid, transfer, manage) using the dropdown.
Develop further targeted measures to reduce the likelihood and impact of your organisation being harmed. Focus on reducing your organisation’s vulnerabilities (exposure).
Look at the Scoring Definitions tab to decide the remaining likelihood and impact scores (after implementing the targeted mitigations) and enter either 1 (VERY LOW), 2 (LOW), 3 (MEDIUM), 4 (HIGH) or 5 (VERY HIGH) for each using the dropdown.
Allocate a risk owner (the accountable), a risk manager (the responsible), and the deadline for achieving the target risk score.
Incident Reporting Procedure
Purpose: The Incident Reporting Procedure identifies why incidents should be reported, defines what an incident is, outlines the four steps of incident reporting, and discusses the Incident Database. (Note, this procedure is not for reporting safeguarding incidents, which should be reported under the Safeguarding Reporting Procedure.)
Why should you report incidents?
All security incidents and near misses that involve anyone working on your behalf should be reported to a Senior Person. This is important because it:
Ensures that immediate support can be provided to the affected individual(s) to reduce any remaining risks to them or others.
Allows you to identify any trends or patterns of incidents you are exposed to and to determine whether any remedial action to prevent the reoccurrence of similar incidents is warranted or whether the security environment is deteriorating or improving.
Provides you with a measurable indicator of whether existing policies and procedures are sufficiently reducing risk or whether alternative approaches need to be explored.
Ensures that you continue to learn from past incidents that have been reported and managed.
What is an incident?
Please review this section and amend as appropriate, including any additional ‘incident affected’ categories to ensure that you include all the incidents that your organisation would like to be reported. Please remember that this procedure does not include the reporting of safeguarding incidents which should be reported under the Safeguarding Reporting Procedure.
Incident reporting process
This section sets out the incident reporting process in four phases: immediate verbal report, written report, incident review, and incident follow-up. You may want to include an additional phase, incident escalation, between immediate verbal report and written report if yours is a large organisation or if it would like additional managers to be informed of all incidents. Please review this section and amend as appropriate, including changing the Senior Person to a role or roles in your organisation.
Incident database
Please review this section and amend as appropriate, including changing the Senior Person to a role or roles in your organisation.
Incident Database
Purpose: The Incident Database allows your organisation to identify any trends or patterns of incidents to determine whether any remedial action is required to prevent future reoccurrence of similar incidents and to provide a measurable indicator of whether existing policies and practices are sufficiently reducing risk.
The Incident Database should regularly feed into the (ideally quarterly) review of the Strategic Risk Register on which safety and security should be a standing risk.
Incident Report Form
Purpose: The Incident Report Form should be used for all incidents (after the immediate verbal report). Each written incident report should outline in some detail what happened and when and how those involved responded. Please ask the affected person to work through all sections of the incident report.
Once an Incident Report Form is submitted, it should be reviewed and entered into the Incident Database and used as the basis for the incident review and incident follow-up process.
Crisis Management Procedure
Purpose: The Crisis Management Procedure defines what a crisis is, outlines the composition of your crisis management team (CMT) and their roles and responsibilities, confirms when a crisis management team should be activated, and provides actions for each phase of a crisis response. This document can be used by both your global CMT and any country CMTs.
When do we use this procedure?
This paragraph provides a definition of a crisis as set out below. You may wish to amend this definition to better describe the things that could cause critical harm to your people or organisation.
An unexpected event or situation that has caused, or has the potential to cause, critical harm to our people, reputation, finances, systems, projects or entire organisation, and thus requires a dedicated crisis management team to manage its impact and aftermath.
Crisis management team structure
A robust CMT includes a range of functions because several different skillsets are required to effectively reduce the impact of a crisis. You may wish to adapt the proposed structure to better fit your organisation, work, and location; however, the following roles are considered critical: Lead, Support, Human Resources, Family Liaison, Media/Communications, and Administration. It is essential that CMT members are selected based on their relevant skills, experience, and personality rather than seniority.
Activating the crisis management team
You should activate a CMT when an incident meeting your definition of a crisis occurs. To help operationalise this definition, it is useful to have a set of ‘activation triggers’ that automatically activate the team. These have been listed in this section of the Crisis Management Procedure. You may wish to amend these triggers to better fit your organisation, work, and location. However, activating a CMT should not be only considered as a ‘last resort’. When there are uncertainties, it is preferable to activate a CMT and then stand it down if not required rather than letting a situation continue until it has definitely reached the threshold of your organisation’s definition of a crisis.
Crisis management phases
This section identifies the phased approach to managing a crisis. It is based on crisis management best practice.
Phase actions
This section assigns specific actions to CMT members at each phase of a crisis. You may wish to amend the specific actions or who they are assigned to as suitable for your organisation, work, and location.
Information and Decision Logs
Purpose: The Information and Decision Logs are used throughout a crisis to log the incoming information, outgoing information, and major decisions taken.
The logs are helpful for several reasons, including the following:
Keeping track of what has happened and at what time.
Reminding CMT members of tasks that need to be completed.
Communicating to other CMT members all the information sent and received and decisions taken so that they have a full picture of the response.
Recording the information, options, and decisions made at the time in case of legal investigation at a later date.
Knowledge Walls
Purpose: The Knowledge Walls are used as one-page visual aids. They remind CMT members of the initial and current situation and provide an essential live record of the crisis response priorities, including the final objective.
Battle Box
Purpose: Your organisation should always maintain a Battle Box, containing the resources and equipment in this list. This saves valuable time when a CMT is activated as the box can be opened and a crisis room set up rapidly without having to locate the required items.
Scenario Plans
Purpose: The Scenario Plan is a template that the CMT members can use to identify future scenarios in a crisis (best, worst, and most likely outcomes).
Regularly completing the Scenario Plan allows the team to develop pre-defined responses, understand factors that can be controlled and influenced, and understand what resources are required to respond. This significantly helps the CMT get ahead of the situation and reduce the number of surprises that can emerge in any crisis.
Learning Management Procedure
Purpose: The Learning Management Procedure details your risk-based learning principles and presents the learning programme available for those working on your behalf based on their role and the level of risk that to which they are potentially exposed.
Learning management principles
This section identifies the key principles and practices to which your organisation commits. You may wish to adapt these to better fit your organisation, work, and location.
Learning programme
This section details the required learning, based on each person’s role and the level of risk to which they are potentially exposed. It also details the required frequency of refresher training. While the training identified in this table is based on best practice, you may wish to amend the roles, learning requirements, and required frequency in order to better fit your organisation, work, and location.
Course explanations
This section provides a description and duration for each course identified in the learning programme. You may wish to adapt the description and duration (which are based on best practice) particularly if you adapted the learning programme.
Accessing learning
Please indicate the person that should be contacted to discuss learning requirements and course access.
Learning Database
Purpose: The Learning Database allows your organisation to record important training information so that you know who has completed what courses when, where, and with what provider and when a refresher course is due. This information will help you to plan when to run training courses and to check if people meet the requirements for specific activities such as travel.
If you amended the courses available in your organisation’s learning programme, you will also need to amend the reference table tab.
Wellbeing Management Procedure
Purpose: The Wellbeing Management Procedure details your organisation’s wellbeing principles and presents the physical and psychological health support that you have made available to those working on your behalf.
Wellbeing management principles
This section identifies the key principles and practices to which your organisation commits. You may wish to amend the principles and practices in order to better fit your organisation, work, and location.
Before employment
This section explains the information provided to potential employees. It is a crucial part of gaining informed consent to provide potential employees with an indication of the stressors and risks that they may face during their employment and as part of their role.
In addition, this section states that your organisation will ask potential employees about how they will manage their wellbeing, so that your organisation and the candidate have the opportunity to discuss the candidate’s ability to manage stress. If you agree to adopt this process, it must be on the basis that it is a helpful conversation that is focussed on identifying any additional support needs that a candidate may have. It is vital that this process does not affect a candidate’s chances of employment, and this should be made very clear to all candidates.
During employment
This section explains the access to health and wellbeing resources, training, and psychological support that employees are provided with during their employment.
The support outlined is extensive so it is important to adapt this section to better fit your organisation, work, and location. Please do not include anything in this section that you feel would not be possible to provide to all your employees.
After employment
This section outlines employees’ access to a wellbeing debrief (at the end of their employment) and psychological support (after their employment).
It is important to adapt this section to better fit your organisation, work, and location. Please do not include anything that you feel would not be possible to provide to all your employees.
Accessing wellbeing support
Please include the contact details of the person who employees should contact to discuss access to wellbeing support. If you have an Employee Assistance Provider or wellbeing provider, you should include their information here as well.
Wellbeing and Resilience Plan
Purpose: The Wellbeing and Resilience Plan is a useful resource for employees and others who work on your behalf. It presents different zones of stress, asking individuals to identify their own personal indicators of stress and strategies to help them get back on track during stressful periods of their lives.
It is important that the plan not be shared, unless the individual completing it chooses to do so. The Wellbeing and Resilience Plan is a confidential document, and organisations must not ask individuals to share them.
There should be no need to amend this plan as it applies to all organisations.
Safeguarding Policy
Purpose: Safeguarding is the responsibility that your organisation has to ensure that staff, operations, and programmes do no harm to children and at-risk adults, particularly in relation to sexual exploitation and abuse. It also entails protecting your staff from bullying, harassment, and discrimination. The Safeguarding Policy details how your organisation achieves these safeguarding obligations. It outlines a clear policy as well as internal and external facilities to disclose safeguarding concerns through the safeguarding reporting system or anonymously through the whistleblowing process.
Our duty of care
This section states that your organisation has a duty to provide safeguarding standards and to take reasonable steps to mitigate any foreseeable harm. It also states that the Safeguarding Policy is designed to protect both children and at-risk adults.
Non-compliance
This section clarifies that the consequences of not following the safeguarding framework is considered a disciplinary matter and may result in disciplinary action up to and including termination of contract. This is included to allow your organisation to act when those working on your behalf refuse to follow your organisation’s safeguarding procedures.
Principles
This section clarifies that the document is underpinned by overarching principles that are informed by the United Nations Convention of the Rights of the Child (UNCRC) and safeguarding best practice. If you do not significantly change the contents of the Safeguarding Policy, you need not amend this section.
Responsibilities
This section details who is responsible for which safeguarding tasks. These responsibilities have been split into different common roles. Please amend the responsibilities so that they are appropriate to your organisation, indicating who is responsible.
Whistleblowing and reporting
This section details and distinguishes the (external) whistleblowing and (internal) reporting procedures. Whistleblowing should only take place if those who have concerns honestly believe that it is in the public interest to use the whistleblowing process. Otherwise, the reporting procedure should be used. Please add the email and phone number for the person in your organisation that staff with safeguarding concerns should report to if it is not reasonable for them to speak to their line manager. You may wish to adapt the whistleblowing and reporting procedures in order to better fit your organisation, work, and location.
Human resources
This section details the safeguarding considerations that your organisation should integrate into its recruitment process. This includes job profiles, job advertisements, interviews, reference checks, proof of identification and qualifications, criminal records check and security clearance, a code of conduct, probationary periods, inductions, and training. You may wish to adapt the human resources section to better fit your organisation, work, and location.
Risk assessment
This section details the key elements of the safeguarding risk assessment and risk reduction measures implemented by your organisation, including ensuring that all partners complete a safeguarding due diligence assessment. You may wish to adapt this section to better fit your organisation, work, and location.
Code of conduct
This section details the commitments that your organisation and those working on your behalf implement when working with children and at-risk adults. This includes safeguarding children and at-risk adults, protection from sexual exploitation and abuse, protection from bullying, harassment, sexual harassment, discrimination and abuse of power, and a code of conduct. You may wish to amend the code of conduct section to better fit your organisation, work, and location.
Reporting
This section details how those who work on your behalf can make a complaint or raise a concern and how complaints and concerns are handled. It lays down the confidentiality around complaints and concerns; the action that will be taken against anyone retaliating against complainants, survivors, and witnesses; and your organisation’s approach to supporting survivors. You may wish to adapt the reporting section to better fit your organisation, work, and location.
See the Safeguarding Definitions for more information.
Safeguarding Reporting Procedure
Purpose: The Safeguarding Reporting Procedure details how your organisation approaches reporting and handling safeguarding complaints and concerns.
Reporting principles
This section details your organisation’s goal of prevention; defines what a safeguarding complaint or concern is and explains why those who work on your behalf need to report them; describes how one can make a report and what happens after a report is made; explains your organisation’s approach to confidentiality around safeguarding; details action taken in situations of retaliation against complainants, survivors, and witnesses; and outlines the survivor-centred approach. You may wish to adapt the reporting principles section to better fit your organisation, work, and location.
Making a report
This section details who to make a report to. Please enter the name of your Safeguarding Focal Point or other person responsible for receiving reports.
Decision-making and investigations
This section details how your organisation handles complaints and concerns, the decision-making process that the Safeguarding Committee will follow, the Safeguarding Committee’s composition, the investigation process, how your organisation will determine whether an investigation is warranted, and how referrals are made to national authorities for prosecution (where the conduct is a criminal act). You may wish to adapt the decision-making and investigations section to better fit your organisation, work, and location. However, we recommend that you make as few adjustments as possible in order to remain aligned with best practice.
Disciplinary process
This section details the extent of possible disciplinary actions and outlines the grievance procedure that can be followed by persons reporting the concern if they are not satisfied with the handling of the concern. You may wish to adapt the disciplinary process section to better fit your organisation, work, and location.
Incident review and follow-up
This section details how incidents are reviewed and followed up. You may wish to adapt the disciplinary process section to better fit your organisation, work, and location.
Safeguarding Code of Conduct
Purpose: The Safeguarding Code of Conduct sets out the safeguarding-related behaviours that those working on your behalf must understand and follow.
The Code is divided into two sections:
Background. Why the Safeguarding Code of Conduct is important and the consequences of not following it.
Agreement. What those who work on your behalf agree to by signing the document.
Please work through the agreement section and amend as appropriate. Once you have a final version in place, it should be signed by all those who work on your behalf and integrated into recruitment and contracting processes.
Safeguarding Report Form
Purpose: The Safeguarding Report Form is used to report safeguarding concerns. It can be completed by a complainant or on their behalf. The form is also used to record the actions taken following a reported concern.
Safeguarding Risk Assessment
Purpose: The Safeguarding Risk Assessment outlines how your organisation assesses safeguarding threats and provides a risk assessment tool and recommended safeguarding mitigations.
Introduction
This section details the three levels of safeguarding risk ratings that are used throughout the document.
Assessing safeguarding threats
This section presents a framework for assessing safeguarding threats based on three criteria and the safeguarding risk ratings.
Safeguarding risk assessment tool
This section assists the assessment of safeguarding risk and asks the user to allocate a risk rating based on their answers to the questions.
Standard safeguarding mitigations
This section presents the recommended mitigations based on the level of assessed risk.
Safeguarding Incident Database
Purpose: The Safeguarding Incident Database allows your organisation to record safeguarding incidents, the outcome of investigations, and details of any follow-up actions. The Safeguarding Incident Database should feed into the (ideally quarterly) review of the Strategic Risk Register on which safeguarding should be a standing risk.
Safeguarding Human Resources Checklist
Purpose: The Safeguarding Human Resources Checklist provides a checklist for Human Resources to use before, during, and after employment.
You may wish to adapt the checklist to better fit your organisation, work, and location.
Travel Management Procedure
You will only have this procedure and its associated resources if you indicated that people in your organisation travel.
Purpose: The Travel Management Procedure identifies the actions that travellers and managers must take to reduce safety and security risks when travelling for work.
Travel management process
This section provides a diagram that represents the travel journey used throughout the procedure. The travel journey includes the following stages: notify, standards, approve, confirm, travel, and return. While you may wish to adapt the details of the procedure itself, we recommend that you retain the original stages of the travel journey.
Step 1 – Notify of intention to travel
This section states that the traveller needs to notify a nominated Travel Manager of their intention to travel well in advance of the planned departure date.
Step 2 – Apply standards
This section details the standards that the traveller and travel manager must ensure are in place prior to the planned departure date. If you indicated that your organisation conducts travel to hostile environments, this section also includes a risk rating and enhanced standards.
Step 3 – Consent to and gain approval to travel
This section details how the traveller provides their own consent to travel and who in your organisation approves the traveller’s request. If you indicated that your organisation conducts travel to hostile environments, this section also includes different risk approvers based on the risk rating of the destination.
Step 4 – Confirm travel arrangements
This section details how the traveller and travel manager should confirm the travel arrangements, following risk and budget approval. Additionally, if you indicated that your organisation conducts travel to hostile environments, this section includes the need for the traveller to attend a pre-travel security briefing.
Step 5 – During travel
This section details the check-in process and actions that are taken if the traveller fails to check-in. If you indicated that your organisation conducts travel to hostile environments, this section also includes different check-in times for travel to different risk-rated destinations.
Step 6 – Return from travel
This section details that the traveller must attend an incident review meeting if they were affected by or witnessed an incident. It confirms that the traveller may be able to access continued physical and psychological support in line with your organisation’s offering.
Annex 1 – Definitions
This annex provides further information on the standards that the traveller and travel manager must ensure are in place prior to the planned departure date. If you indicated that your organisation conducts travel to hostile environments, this section also includes enhanced standards. If you have amended any of the travel standards, you will need to amend this section as well.
Trip Form
Purpose: The Trip Form should be completed by the traveller. It contains details of the trip, travellers, activities, flights, accommodation, internal and external contacts, and confirmation that the standards have been met and provides an area for traveller consent and approval.
If you indicated that your organisation conducts travel to hostile environments, the form also includes the Travel Risk Assessment (below) and a contingency plans section that should be completed for travel to HIGH and VERY HIGH risk-rated destinations.
Travel Risk Assessment
Purpose: If you indicated that your organisation conducts travel to hostile environments, the Travel Risk Assessment should be completed for travel to HIGH and VERY HIGH risk-rated destinations.
To complete the Travel Risk Assessment, follow these steps:
List the potential threats that your travellers could be harmed by and describe why they are vulnerable to each threat.
Look at the Scoring Definitions tab to decide likelihood and impact scores (without implementing any mitigations) and enter either 1 (VERY LOW), 2 (LOW), 3 (MEDIUM), 4 (HIGH) or 5 (VERY HIGH) for each using the dropdown.
Identify measures that can be put in place to reduce the likelihood and impact of the traveller(s) being harmed. Focus on the vulnerabilities.
Look at the Scoring Definitions tab to decide the likelihood and impact scores (after implementing the mitigations) and enter either 1 (VERY LOW), 2 (LOW), 3 (MEDIUM), 4 (HIGH) or 5 (VERY HIGH) for each, using the dropdown.
Send the risk assessment to the risk approver who will review and either approve or decline the travel. The latter could include asking for further mitigations to be implemented to reduce the risk to within your organisation’s risk appetite so that the travel can proceed.
Proof of Life Form
Purpose: If you indicated that your organisation conducts travel to hostile environments, the Proof of Life Form should be completed for all travel to HIGH and VERY HIGH risk-rated destinations.
What is a Proof of Life form?
This section explains that Proof of Life is essential in abduction management and fulfils two functions:
Verifies claims by a group that it is holding the abductees or has contact with the group holding them. Proof of Life is vital to distinguish real abductors from opportunists or from groups that may have held the abductees at some point but are no longer holding them.
Confirms that the abductees are still alive.
Completing the form
This section outlines several explicit agreements of which the person completing the Proof of Life Form needs to be aware. If you chose to adapt the form to better fit your organisation, work, and location, you may also need to amend these explicit agreements.
Updating the form
This section confirms that any changes to Proof of Life Forms must be made through the submission of a new form. It is vital that this section remain in the form as Proof of Life Forms should only be accessed in the event of a (confirmed or suspected) abduction or detention and not for any other reason including editing.
Form access
This section confirms who in your organisation has access to completed Proof of Life Forms and who may be provided with some or all the information contained within them. You may wish to adapt this section to better fit your organisation, work, and location. However, you should only amend the internal people detailed section and not the disclosure to others one as that is a legal requirement in many countries.
Emergency contact information
This section details the primary and secondary emergency contacts selected by the person completing the form.
Your acceptance and agreement
This section asks the traveller to accept and agree with several specific statements. We do not recommend that you amend this section other than where indicated in red.
Process for contacting your emergency contacts
This section details how your organisation will contact the primary and secondary emergency contacts selected by the person completing the form. We do not recommend that you amend this section.
Your personal medical details
This section is the first of four sections in which the person completing the form has the option to give or not give consent. In this case, they are asked to consent to sharing their personal medical details with your organisation. If they choose to consent, they are asked to provide relevant information. We do not recommend that you amend this section other than where indicated in red.
Providing abductors and other specified persons with personal medical details may be relevant in identifying and treating them if they become ill or wounded or have a pre-existing medical condition or require medication.
Your phone and debit and credit card details
This section is the second of the four sections where the person completing the form has the option to give or not give consent. In this case, they are asked to consent to sharing their phone and debit and credit card details with your organisation. If they choose to consent, they are asked to provide relevant information. We do not recommend that you amend this section other than where indicated in red.
Providing law enforcement or government agencies access to phone and debit and credit card data after an abduction has occurred may provide them with an understanding of when and where these may be used or may provide details of where the individual is held or where persons connected with the abduction are active.
Your social media account details
This section is the third of the four sections where the person completing the form has the option to give or not give consent. In this case, they are asked to consent to sharing their social media account details with your organisation. If they choose to consent, they are asked to provide relevant information. We do not recommend that you amend this section other than where indicated in red.
Providing law enforcement or government agencies access to social media accounts after an abduction has occurred may allow them to suspend their accounts to limit their usefulness to the abductors and limit media intrusion (e.g. accessing photos or contacting family members or friends).
Your photographic representation
This section is the last of the four sections where the person completing the form has the option to give or not give consent. In this case, they are asked to consent to sharing their photographic representation with your organisation. If they choose to consent, they are asked to provide relevant information. We do not recommend that you amend this section other than where indicated in red.
Your Proof of Life questions
This section is where the person completing the form enters five Proof of Life questions and answers, considering the following:
They should select questions to which they will always remember the answers.
The questions should be specific. General questions, such as the name of a pet, may be easily ascertained, for example from social media.
The questions should refer to something special in their life. If possible, the question should help trigger a positive memory and instil hope in them.
The questions should not relate to potentially sensitive issues such as politics, religion, gender, sexual identity, or alcohol/drug use.
Abduction Management Procedure
You will only have this procedure and its associated resources if you indicated that your organisation either has people who travel to hostile or insecure locations or if you indicated that your organisation has a permanent presence in overseas locations that are high risk.
Purpose: The Abduction Management Procedure details your organisation’s abduction management principles, responses, Proof of Life process, communicators, external actors, communications, and continuity activities.
Principles
This section details the key policy positions of your organisation.
You should adapt this section to better fit your organisation, work, and location, specifically reviewing (and where relevant amending) the bullet points related to non-payment and facilitation of ransom.
It is your organisation’s decision whether or not to pay or facilitate ransoms. This decision is extremely complex and involves multiple considerations including the following:
Your organisation’s ethical stance on ransom payments
Anti-terrorism legislation and sanctions
Different legal jurisdictions
Funder conditions
Crisis response (kidnap, ransom, and extortion) insurance
Organisational response capacity
If you are not certain of the positions to take regarding ransom payment and facilitation, we strongly recommend that you request support from Open Briefing.
Response
This section details your organisation’s response to a suspected or confirmed abduction, including the actions that the CMT will take during the first hour, 1-2 hours, 2-6 hours, and 6-12 hours.
Sequence of events
This section provides a flow chart representing the common sequence of events in an abduction situation. This is provided so that CMT members are clear on the possible events that will occur and the actions that should be taken in managing a suspected or confirmed abduction situation.
Resolution
This section provides guidance, actions, and considerations in the event of the release of an abductee or the unsuccessful resolution of an abduction.
Proof of life
This section details why Proof of Life is an essential tool in abduction management, discusses the Proof of Life methods commonly available, and confirms the Proof of Life process.
The Abduction Management Procedure must remain confidential and restricted to your crisis management team and senior management. It should not be shared with others as it contains information that would be useful to abductors or other stakeholders involved in the case.
Further information is available in the Abduction Management guidance.
Abduction Incident Report Form
Purpose: The Abduction Incident Report Form should be used for all suspected or confirmed abductions. Each written report should include headline information, reporter information, incident information, and subsequent steps.
The Abduction Incident Report Form should be completed either by the Senior Person in the country where the abduction has taken place or by the Lead or Support on the CMT.
Country Management Procedure
You will only have this procedure and its associated resources if you indicated that your organisation has a permanent presence in other countries.
Purpose: The Country Management Procedure details how your organisation’s programmes and offices in other countries can reduce their risk by developing and implementing a Country Security Plan. Each office or programme should complete their own specific Country Security Plan.
The Country Management Procedure presents the structure of the Country Security Plan, providing an overview of the following four documents that each country needs to complete:
Welcome Pack
Context Analysis
Country Risk Assessment
Standard Operating Procedures (SOPs), Contingency Plans, and Crisis Management Team (CMT)
Finally, the Country Management Procedure also details when countries should update their Country Security Plans as follows:
For all locations. Whenever there is a significant change in the local context plus once a year.
For high-risk locations. Whenever there is a significant change in the local context plus either once per year, once every nine months, or once every six months depending on the risk rating.
Unless you intend to change either the structure of the Country Security Plan or the content of any of the four documents, it is not necessary to amend the Country Management Procedure itself.
Welcome Pack
Purpose: The Welcome Pack is the first of the four documents that make up the Country Security Plan. The purpose of the Welcome Pack is to provide useful security information and practical guidance for visitors.
The Welcome Pack should do the following:
Provide key facts about your organisation’s operations in the country
Detail the top threats and mitigation measures for the country
List what visitors need to do before, during, and after travel
Provide other useful information (e.g. entry requirements, transportation, accommodation, money and banking, communications, climate, dress, local customs, etc.)
Identify any entry and departure requirements and processes
List important and emergency contact details
Translate essential words and phrases
To make it easier for staff to understand how to complete the Welcome Pack, we have provided examples directly in the document. However, it is vital that each overseas office or programme country adapts the Welcome Pack to better fit their organisation, work, and location. Under no circumstances should they accept the examples provided as these will not fit the local security context.
Context Analysis
Purpose: The Context Analysis is the second of the four documents that make up the Country Security Plan. The purpose of the Context Analysis is to detail the context of both the country and your organisation in the country so that the office or programme can analyse the threats and vulnerabilities that arise from both.
The organisational context includes headline information, activities, human resources, reputation, offices, operating locations, and vehicle fleet (if relevant). The country context includes the sector, demographics, economy, education, politics, conflict, crime, security trends, religion and ethnicity, infrastructure and climate, communications and digital security, health, and increased exposure to risk. Each of these sections in the Context Analysis include a prompt to explain what information is relevant.
In each section, the person completing the document should outline how the factor affects the safety, security and wellbeing of your organisation and those who work on your behalf, focussing on specific threats.
Country Risk Assessment
Purpose: The Country Risk Assessment is the third of the four documents that make up the Country Security Plan. The purpose of the Country Risk Assessment is to help an office or programme in another country understand the threats present in that country so that they can develop appropriate measures to reduce risk.
To make this process simpler, the office or programme will need to complete the following five steps:
Identify the threats present in the country context by drawing on the Context Analysis.
Identify the reasons why your organisation’s operations and people in that country are vulnerable to each threat.
Score and describe the likelihood and impact of each threat affecting your operations or people.
Develop mitigation measures to reduce the level of risk.
Score and describe the likelihood and impact of each threat affecting operations or people after the mitigation measures have been implemented.
To make it easier for countries to understand how to complete the Country Risk Assessment, we have provided guidance throughout the spreadsheet.
The Country Risk Assessment process can be somewhat subjective. As such, the process should be participatory and should include a range of internal stakeholders and not only senior managers. A great way of doing this is running a risk assessment workshop with people with different roles and at different levels of seniority.
SOPs, Contingency Plans, and CMT
Purpose: SOPs, Contingency Plans, and CMT is the fourth of four documents that make up the Country Security Plan.
To make it easier for staff to understand how to complete the SOPs, Contingency Plans, and CMT document, we have provided examples directly in the document. However, it is vital that each overseas office or programme country adapts the document to better fit their organisation, work, and location. Under no circumstances should they accept the examples provided, as these will not fit the local security context.
The document has three elements as follows:
Standard Operating Procedures (SOPs). Detail the security measures that the office or programme in that country implements to reduce their risk. This allows them to be clearly communicated in writing to all relevant people in the country.
Contingency Plans. Detail the actions that the office or programme will take if the context changes. There are three contingency plans: scenario, programme, and medical.
Crisis Management Team (CMT). Identifies the people who are members of the country-level CMT.
Disclaimer: To the fullest extent permitted by law, Open Briefing will not be liable for any loss, damage or inconvenience arising as a consequence of any use or misuse of this resource.
Copyright © Open Briefing Ltd, 2020. Some rights reserved. Licensed under a Creative Commons Attribution-NonCommercial 4.0 International Licence.
Last updated
Was this helpful?